Hello, it’s the end of the 404CTF so let’s do a writeup of a challenge I loved.
Frida-Me
First of all, you can see the name of the challenge : frida-me, it’s already a free tip for you. You know you will not need to reverse something or deobfuscate an apk, you’ll use Frida (https://frida.re/docs/android/)
Launch the App
Nothing difficult for the moment, it’s interesting to launch the app to understand how to get the flag. I used a VM from Android studio and installed the app using adb commands.
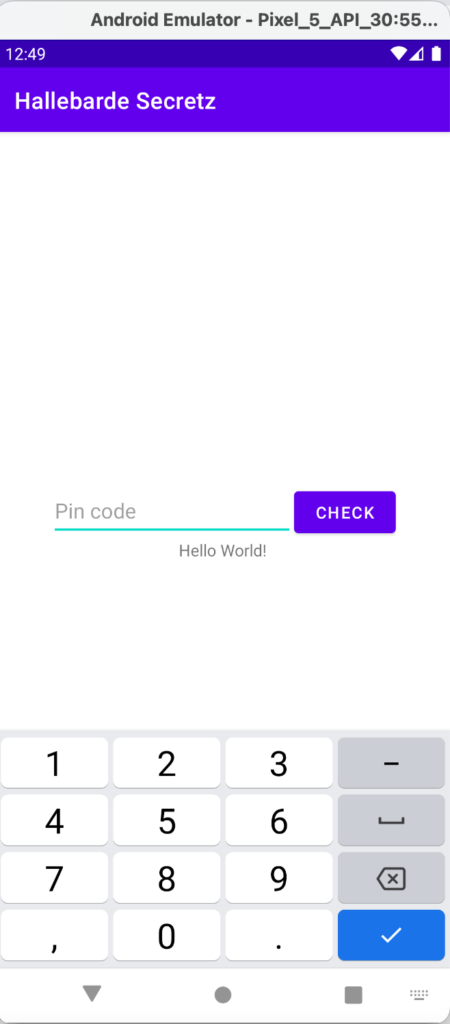
Uhhh, so we can see the password is a pin. One idea would be to directly use a macro and try a lot of passwords but it would take too much time. Let’s decompile the app to understand it !
Jadx java decompiler
I used an online java decompiler to decompile my app and investigate further. Jadx will give you 2 folders : one containing resources (images, Manifest, etc…), the other will contain the java code. You can find the archive right here :
Investigate Main Activity
On Android, every launched screen you see is called an “Activity”. The activity which loads the first is called the Main Activity. It can be renamed but you can always find the path to the main activity by reading AndroidManifest.xml, the name of the first activity will be shown in this line :
<activity android:name="p004de.hallebar.secretz.MainActivity" android:exported="true">
Thank to this information, we can now navigate to de/hallebar/secretz and open MainActivity.java.
Understanding the Java code
Actually, this challenge is easy : there is (almost) no obfuscation and it facilitates our investigation.
On Android, the Java method onCreate(Bundle bundle) is called to create the Activity. It’s naturally the method we want to investigate.
We can see in the line 47 :
...
if (obj.length() <= 8) {
//doing stuff..
}
activityMainBinding.sampleText.setText("Pin code too long");Bingo ! We can see the pin code is shorter than 8. What does it mean ? We don’t need to reverse any method to find the pin, we can bruteforce it with Frida. But we first need to understand which method is called to check the pin….
Line 54 :
activityMainBinding.sampleText.setText(mainActivity.complicatedCheckerPleaseDontReverse(Integer.parseInt(obj)));We can see the pin we enter is checked by this method : complicatedCheckerPleaseDontReverse. The entry of this method is an int and it outputs the password if it’s correct, or an error as a TextView.
Using FRIDA
Now we have all the elements we need to use Frida. I recommend to use a rooted device to launch Frida, it’s easier and faster. With a VM from Android Studio, you can use the command “adb root” to root the VM.
Step 1 : install frida (pip install frida-tools), download the frida-server binary (ARM or x86 depending or your Android VM) and put it in data/local/tmp in your Android device (don’t forget to give the execute permission).
Step 2 : Launch the frida server : ./frida-server… &
Step 3 : create a script to hook the check method. You can use either python or js. I make a js script :
console.log("Hook successfull");
Java.perform(function x() {
console.log("Inside java perform function");
var mainActivity = Java.use("de.hallebar.secretz.MainActivity");
mainActivity.complicatedCheckerPleaseDontReverse.overload("int").implementation = function (x) { //hooking the method and overwritting it
console.log("Function called");
let i = 0;
while (i < 99999999) { // bruteforce the pin
var ret_value = this.complicatedCheckerPleaseDontReverse(i);
console.log("returning "+ret_value);
if(!ret_value.includes("Wrong")){
console.log("GZ")
return ret_value;
};
i++;
}
return ret_value;
};
});Step 4 : : check the pid of your app with frida-ps -U (-U is to connect to your Android Device)
Step 5 : launch the script :
frida hallebard_pid -U -l myscript.jsWait one minute …
Enter a random password and click on the “check” button in the app to start the bruteforce.
After few seconds/minutes, the flag will appear in the output of the console with a message.
GZ !